
DNS Response Policy Zones (DNS RPZ) is a method that allows a name server to be configured with information on top of the global DNS to provide alternate responses to queries.
One of the original purposes for DNS RPZ was to provide "DNS Firewall" capabilities. DNS RPZ was originally created to protect internet users from an ever-expanding list of threats, exploits, and attacks. While DNS RPZ excels at providing users protection, it also provides ancillary benefits and can be used to serve a wide variety of other use cases. Here are a few:
- DevOps
- Static NAT
- Split Horizon DNS en...
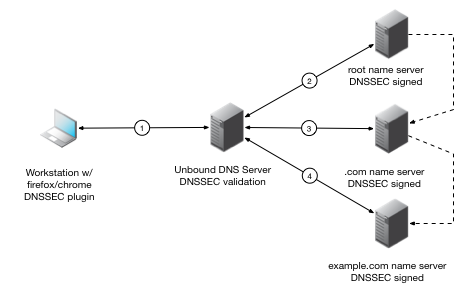
Configure the high-performing recursive Unbound DNS server with DNSSEC validation on Linux.
Given all the hoopla surrounding the topic of DNSSEC, it's definitely time to get prepared for it. After all, the last of the root name servers ( J-ROOT ) will all be serving a Deliberately Unvalidatable Root Zone or (DURZ) by May 5th. On July 1st however, there will be distribution of a validatable, production, signed root zone. Signing of the root zone is key for creating the "chain of trust" or a secure delegation hierarchy. DNSSEC securely signed zones vouch for their children's keys, but...

Unbound is an open standards high-performing validating, recursive, caching DNS resolver.
Unbound is a validating, recursive, and caching DNS resolver. Unbound is developed and currently maintained by NLnet Labs, a non-profit, public benefit foundation. It is based on the ideas and algorithms taken from a Java prototype developed by Verisign Labs, Nominet, Kirei, and ep.net. Unbound was released to the public in May 2008 under the BSD Licensing model which allows its use in other products without any major restrictions. In this article, we’ll discuss ten (10) reasons to use Unbound...

In-depth details on the tools and "Smart Sign" functionality in Bind 9.7.0
The last article discussed the basics of the BIND 9.7.0 "Smart Sign" feature. In this article, we expose additional functionality that has been incorporated into the software to make it much simpler to sign, operate, and maintain DNSSEC signed zones. This article will help tie in some of the information provided in the previous article, Bind 9.7.0 - Part 2, New DNSSEC key metadata. Bind 9.7.0 takes an interesting approach to automating DNSSEC key lifecycle maintenance, leveraging local Dynamic DNS enabled zo...

DNSSEC keys are now automatically imported directly into the zone using the new Smart Signing feature introduced in BIND 9.7.0
In our previous article, we covered how BIND 9.7.0 embeds timing metadata directly in DNSSEC keys as its method for DNSSEC key lifecycle management. In this article, we discuss the new BIND 9.7.0 Smart Signing feature and how it improves and simplifies the process of signing a single zone.
With all the DNSSEC related changes in BIND 9.7.0, it should come as no surprise that many of the BIND-provided utilities have been updated, and a few new ones have been a...

DNSSEC private key file format has been extended to contain key timing metadata, allowing the administrator to schedule when a key will be scheduled, published, and revoked.
One of the most glaring new features to Bind 9.7.0 is in the area of DNSSEC key lifecycle management, which includes the generation, publication, revocation, and eventual deletion of DNSSEC keys as it pertains to signing zones and performing DNSSEC key rollover. Presently, there are a number of different DNSSEC tools frameworks such as DNSSEC-TOOLS and OpenDNSSEC which have their own suite of scripts, services, and...

The release of BIND 9.7.0 has been called the "DNSSEC for Humans" because it offers significant leaps in functionality and automation that is more simple to use.
To date, implementing DNSSEC using ISC Bind was manually intensive and complicated at best. Following the general availability of Bind 9.7.0 on 02-16-2010, the task is not nearly as daunting. In this article we review at a high level, some of the new changes, features, and enhancements that have been incorporated in Bind 9.7.0 in support of DNSSEC. This several part series will cover:
- New DNSSEC key metadata and lifecycl...
